Over the past year, Australian companies and governments have grappled with a series of significant data breaches, amplifying concerns about the nation’s cybersecurity landscape. According to the Australian Signals Directorate’s (ASD) Annual Cyber Threat Report, there has been a notable 14% surge in the cost per breach to businesses and a 23% increase in reported cybercrime incidents compared to the 2021-2022 year. These statistics underscore the escalating cyber threat confronting Australian individuals and businesses. With this increased cyber security threat, greater emphasis is being placed on secure development and threat modelling in accordance with the concept of “shifting left”. Security conscious companies like Xelleron are embracing this philosophy, providing a pathway into the software security industry for new interns like me.
My journey into the realm of security started in early 2021 when a conversation about Dungeons and Dragons led me to meet Stephen Kho, the Director of Offensive Security at Gen Digital.
Stephen generously mentored me, providing insights into the security industry, available learning resources, and course options at the University of Queensland. This mentorship led to an enriching work experience opportunity at Xelleron, a Software as a Service (SaaS) company based in Brisbane.
Xelleron was taking steps towards security certification and Stephen was a senior security professional with experience in the industry. This alignment paved the way for a unique opportunity to learn and develop skills at Xelleron, allowing me to work mentored by Stephen Kho, while contributing to the company’s commitment to secure development.
Shifting Left at Xelleron
Xelleron’s approach to security was informed by the concept of “shifting left.” Unlike the traditional reactive response to pentest results or breaches, “shifting left” is about proactive measures at each stage of the secure development lifecycle to prevent vulnerabilities. The three key steps in this approach are training, designing, and developing.
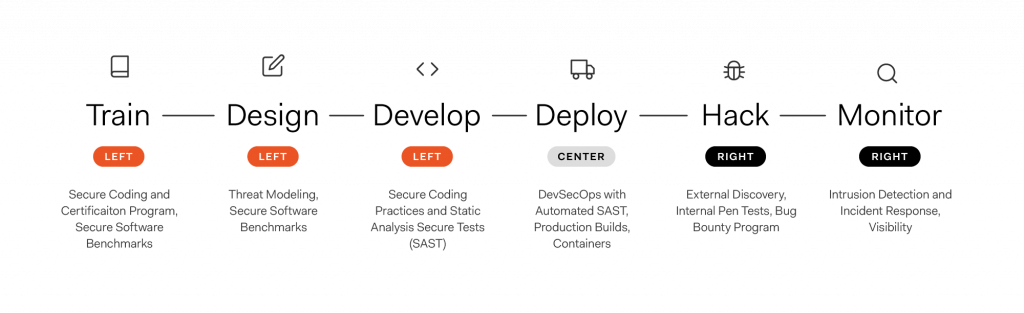
The Importance of Documentation
Stephen introduced me to the concept of a security policy, a document with a company wide scope outlining commitments to security standards. This living document evolves over time, adapting to new practices and serving as a guide in each stage of the secure development process. This was the first step in learning about the extensive documentation essential in maintaining security practices. Once followed, this documentation can serve as the best shield against phishing, ransomware and other common security breaches.
Tasked by Xelleron, I started the process of documenting the existing security practices into a policy. Previous intern Scott Maher had identified Snyk as a great tool for Software Composition Analysis (SCA) and Static Application Security Testing (SAST). Using the Snyk extension in a developer’s environment you can detect vulnerabilities and learn about them from Snyk and CWE (Common Weakness Enumeration). This low-cost, low-maintenance solution proved instrumental in creating a procedure to encourage learning and participation in security practices.
Following a security policy, procedures must be documented to ensure compliance with the standards set out. Utilising the Snyk tool, a procedure was to be created to ensure uniform completion of the necessary steps to keep track of detected vulnerabilities in Xelleron’s security.
Logging emerged as a key element in this procedure, offering insights into the lifecycle of a vulnerability and enabling developers to learn through previously logged solutions as well as Snyk’s resources. Leveraging GitHub features such as issues, templates, and workflows, we established a system that was easy to use while encouraging learning and tracking useful metrics for evaluating security progress.
My Internship Experience
During my time at Xelleron, I was able and encouraged to ask questions and learn from team members including senior staff. This rare environment meant the team at Xelleron enabled me to immerse myself in threat modelling, GitHub workflows, Xelleron’s custom environment, API’s and integrations as well as security tooling, documentation, and principles. I’ve been able to hone skills in YAML, DFD creation, and producing security policies and procedures, contributing to Xelleron’s journey toward a proactive “shifting left” approach and obtaining future security certificates.
My internship at Xelleron has been an invaluable experience, highlighting the significance of security in software engineering. I’ve learnt that the “shifting left approach”, coupled with documentation and tooling, not only enhances the security of a company but also sets the stage for a sustainable and gradual security journey.